As we rapidly approach Q4 (or possibly have just entered Q4 depending on when you read this), one of the foremost concerns on many small and medium-sized business owners’ minds is their fiscal year tax liabilities. No one loves paying the tax man — obviously — but if you think ahead and plan shrewdly, you can invest in critical areas … Read More
Why you absolutely should update your iPhone iOS… now
Apple has been making their case to consumers over the last few months and years as the privacy-focused alternative to big-brother-ish Amazon, Facebook and Google (at least, that’s the implication in Apple’s PR positioning, anyway). But no matter how privacy and security focused you may be as a company — especially if you’re a massive, strategically vital company like Apple … Read More
IT budgets grow despite economic uncertainty
For years — maybe decades — management viewed IT as primarily a cost center. A necessary evil, at an often heavy expense, to enable the rest of the company to simply function. Given that prevalent mindset, most business leaders strove to keep IT budgets down as much as possible. The thinking went that if it wasn’t actively improving sales or … Read More
Living off the Land cyber attacks — your newest nightmare
We talk a lot about looming cyber threats out there. It’s a huge operational concern for businesses large and small. Insurance, backup, protection, you name it — we’re writing about it and talking about it with our clients and partners. What was a relatively small part of our managed services portfolio not too long ago has become a central tenet … Read More
Safari hack shows browser security key to cyberdefense
In news you may have missed, Apple awarded a bug bounty for more than $100k back in January. The bug identified was a clever and creative vulnerability in the Safari browser system which could have allowed hackers to exploit target systems, implant malicious files and code on host computers, impersonate users with accurate credentials, commandeer webcams and microphones, etc. This … Read More
Russia increasing cyber attacks globally — how to protect your business
As Russia’s invasion of Ukraine drags on — and global sanctions against Russia take firmer hold — cyber attacks coming from Russia have started to both increase in frequency as well as severity. For nearly a decade, Russia has perfected state-level cyberwar by practicing on Ukraine. Now, however, Russian-originated cyber attacks are leaking out to government entities and private corporations … Read More
Microsoft debuts New Commerce Experience, changes to 365
The various Microsoft 365 offerings are the backbone of many enterprises. A huge percentage of our clients and partners rely on some combination of Microsoft 365, Office 365, Dynamics 365 and Power Platform subscriptions. To that end, Microsoft has recently changed how these products are purchased and how they’re priced. The company is calling this the “New Commerce Experience” (NCE), … Read More
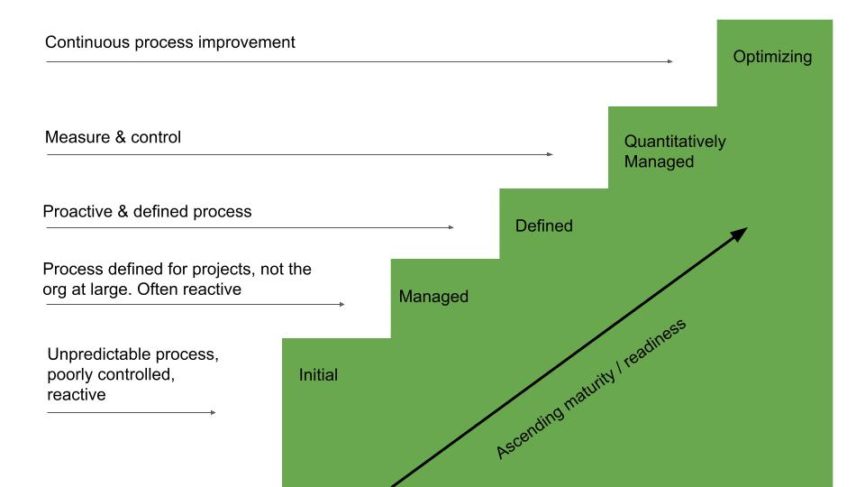
The stages of vulnerability management
Cybersecurity and organizational preparedness have never been more important than they are right now. Both will become more important with every passing week. More advanced, more pervasive and more destructive cyber threats crop up every single day, and your vulnerability management plan has to be up to snuff to keep your company and its clients safe. But where do you … Read More
Cybersecurity tiers: how to move from Tier 1 to Tier 4 of preparedness
Back in 2018, the National Institute of Standards and Technology released a report with a pretty bland name: Framework for Improving Critical Infrastructure Cybersecurity. But in that report is one of the most useful guides for how to think about organizational cybersecurity, how to improve your cybersecurity and how to stay secure even in a rapidly evolving threat environment. We … Read More
2022 Cybersecurity Predictions
Sometimes, I wish I didn’t have to write about cybersecurity quite as much as I do. If it wasn’t such a dangerous and pervasive menace, I wouldn’t have to spend so much time researching it and writing about it. But as you can imagine, cyber threats are only getting more common, more widespread and more destructive. And for business owners … Read More









Dive straight into the feedback!Login below and you can start commenting using your own user instantly