Cybersecurity and organizational preparedness have never been more important than they are right now. Both will become more important with every passing week. More advanced, more pervasive and more destructive cyber threats crop up every single day, and your vulnerability management plan has to be up to snuff to keep your company and its clients safe. But where do you begin? How do you design a vulnerability management plan that can not only respond to incursions today, but predict and proactively prevent them in the future?
It all begins with the capability maturity model.
Capability maturity model
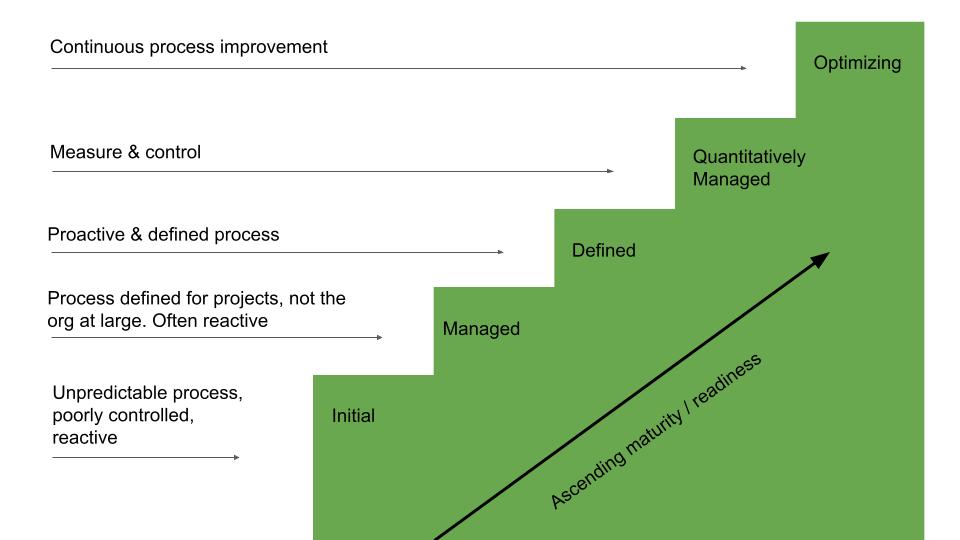
The idea behind a vulnerability management plan is to recognize what it is you need, define it, implement it, expand it across all business units and then evolve into a state of continuous improvement. This maturity model exists for the lifecycle of any business process, especially in the field of software development and implementation. This model helps develop and refine a process in an incremental and definable method, which is key to long term success in any process deployment. So, we apply this model approach to vulnerability management as well.
Stage 1: Initial
For companies in this stage, there are generally no or minimal processes and procedures. You might hire a third party vendor to perform stress tests and incursion drills, but once you patch any vulnerabilities, companies that remain in this stage are still very vulnerable to attacks. Security can’t just be a once or twice a year checkbox, but a continuous process of improvement.
Stage 2: Managed
In the managed stage, vulnerability scanning is incorporated into standard business protocols. It happens frequently and repeatedly. But, most organizations that remain in this stage suffer from a couple of common issues. First, they often don’t have enough money to buy or employ a high-level, state-of-the-art scanning and detection system. And secondly, if this isn’t prioritized and funded adequately from upper management, they often have neither the staff nor the resources to accurately prioritize which vulnerabilities to patch first (or fully patch them at all).
Stage 3: Defined
If you rise beyond Stage 2, the processes and procedures become both well-characterized and understood throughout the organization. Your cybersecurity and IT teams have support from upper management and trust from system administrators.
As the Center for Internet Security recommends, these orgs run vulnerability scans once a week (at minimum). The scans then populate business-unit specific reports with recommendations tailored to their working environments and threat vectors. System admins receive specific vulnerability reports while management receives risk trending reports.
Stage 4: Quantitatively Managed
In the Quantitatively Managed stage of a vulnerability management program, you move beyond defining processes and protocols with generalized reports for specific business units to having quantifiable, specific attributes the program tracks and delivers to management and system admins. Everything can be boiled down to hard and precise data that’s actionable across all parts of the organization.
Stage 5: Optimized
Taking the step up to Stage 5 optimization requires not only the precise data inputs and intel from Stage 4, but also a plan and process for markedly improving any and all areas of deficiency identified in Stage 4. This is about implementation, not just reporting. It’s not enough to know every possible vulnerability as dictated by your vulnerability management plan, but rather to make quantifiable, data-backed improvements across those vulnerabilities.
This is a continuous process that requires company-wide dedication and emphasis. And once you’re optimizing each of the metrics identified in Stage 4, you’re massively reducing the attack surface of the wider org.
In closing
I realize that’s a lot to digest, especially if you’re still on the lower rungs of the maturity ladder. That’s no problem! Because that’s quite literally what we are here for. We help small and medium-sized businesses take their vulnerability management to the next level with our guidance and expertise every step of the way. Drop us a line today, and let us show you how we can help protect your business.

Dive straight into the feedback!Login below and you can start commenting using your own user instantly