The Cybersecurity and Infrastructure Security Agency (CISA) recently released a detailed report about the ransomware-du-jour, BlackMatter. Similar to other Ransomware-as-a-Service threat vectors (which we’ve written about before), it’s cheap and easy to deploy, utterly devastating to infected systems, and cause for real concern in the IT community. I wish this wasn’t such a tired story, but this is life in … Read More
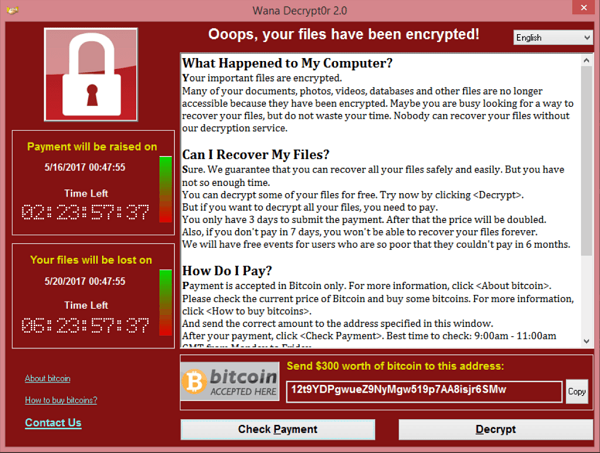
$10 billion lost, a global supply chain crippled, and a miracle mistake: A NotPetya primer — cyberattack of the century
If it hadn’t been for Somali pirates, Navy Seals or the Tom Hanks movie Captain Phillips, chances are you probably wouldn’t have heard of A.P. Moller–Maersk Group, or ‘Maersk’ for short. It’s one of those companies content to work in the background, unnoticed and unknown, while at the same time fueling the entire world economy. It’s one of the largest intermodal logistics … Read More
Ransomware is a huge and growing problem — here’s 4 ways to protect your business
All the trend lines point one direction when it comes to ransomware frequency and scope of damage — up and to the right. A report from Cybersecurity Ventures projects that on average, there will be a ransomware attack on a business every 14 seconds by the end of 2019 — up from a rate of one attack every 40 seconds … Read More
Proactive Service vs Reactive Support
When we talk with business leaders we often hear about their perception of Proactive Service vs Reactive Support. Many business have been told that Proactive Support includes things like patch updates, anti-virus checks, computer monitoring, and so on. While you can consider these items to be proactive in nature, doing them independently doesn’t offer much value to the end result … Read More
Staff Time Management
We’ve noticed a trend in the past couple of years in our business and with our clients as well. As a business matures and grows the people in that business must do the same. The Financial Times points out that Staff Time Management is one of the key differentiators between growing firms and those that stagnate (ref: https://goo.gl/zu0tX6). The logistics … Read More
The Leverage Service Experience
The Leverage Service Experience is unique. It’s like the feeling you get when you go home for Thanksgiving. You don’t use it everyday, but when you do it feels comfortable and familiar. The person you talk to knows who you are and what you like. They know how you like to be treated and how you want your computer to … Read More
Data Backup Testing
We recently went through a new client acquisition that required us to use backups to install their new server because the old server was in the cloud far away. The process was pretty painful because the former IT company didn’t have proper backup systems in place. This made me think of some other issues we’ve encountered with backups for new … Read More




Dive straight into the feedback!Login below and you can start commenting using your own user instantly