A VPN, or virtual private network, is a hallmark of good cybersecurity defense. Most companies utilize some form of VPN these days, and with good reason. As Kaspersky puts it, “VPNs encrypt your internet traffic and disguise your online identity. This makes it more difficult for third parties to track your activities online and steal data. The encryption takes place in real … Read More
The most successful phishing attacks… come from you
It’s a bit exhausting being an online person in 2022. Hyper-vigilance is the price we all have to pay to exist online or work online, which is a prerequisite for almost any business these days (at least in some form or fashion). But, there’s no end to spam emails, phishing emails, malware, ranomware, you name it. As an individual, some … Read More
Why you absolutely should update your iPhone iOS… now
Apple has been making their case to consumers over the last few months and years as the privacy-focused alternative to big-brother-ish Amazon, Facebook and Google (at least, that’s the implication in Apple’s PR positioning, anyway). But no matter how privacy and security focused you may be as a company — especially if you’re a massive, strategically vital company like Apple … Read More
The stages of vulnerability management
Cybersecurity and organizational preparedness have never been more important than they are right now. Both will become more important with every passing week. More advanced, more pervasive and more destructive cyber threats crop up every single day, and your vulnerability management plan has to be up to snuff to keep your company and its clients safe. But where do you … Read More
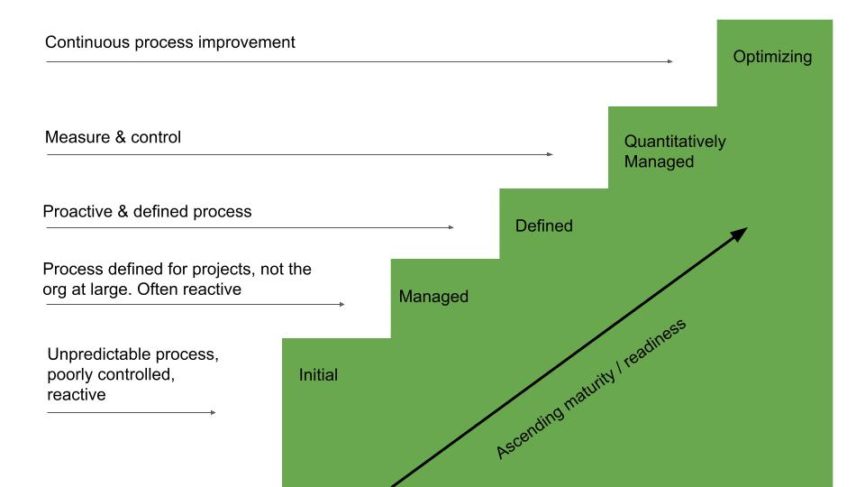
Cybersecurity tiers: how to move from Tier 1 to Tier 4 of preparedness
Back in 2018, the National Institute of Standards and Technology released a report with a pretty bland name: Framework for Improving Critical Infrastructure Cybersecurity. But in that report is one of the most useful guides for how to think about organizational cybersecurity, how to improve your cybersecurity and how to stay secure even in a rapidly evolving threat environment. We … Read More
2022 Cybersecurity Predictions
Sometimes, I wish I didn’t have to write about cybersecurity quite as much as I do. If it wasn’t such a dangerous and pervasive menace, I wouldn’t have to spend so much time researching it and writing about it. But as you can imagine, cyber threats are only getting more common, more widespread and more destructive. And for business owners … Read More
Your biggest cybersecurity threat in 2022 may just be… burnout?
There might never have been such a ripe time to experience professional burnout. We’re rounding the corner into Year 3 of a global pandemic; we’ve spent much of the last two years in some form of lockdown, juggling a new working reality all while figuring out child care, education, you name it… add in trying to maintain some semblance of … Read More
Cyber insurance: why you need it, what it takes to qualify
We’ve written time and time again about protecting your company and its assets from cyber attacks. Threat vectors are multiplying in both form and function while the rise of ransomware-as-a-service should give any business leader nightmares for how accessible it makes carrying out sophisticated cyberattacks to would-be hackers. So what do you do? How do you protect yourself against downside … Read More
IT management vs cybersecurity
IT management and cybersecurity go hand in hand. There are few companies in 2022 that can be successful without high-level performance on both fronts. For most small and medium-sized businesses, these may not even be treated as separate functions or departments, but rather lumped together into the “technology” bucket (which isn’t exactly wrong, either). But, there are important distinctions between … Read More
Critical Apache Log4j vulnerability — what you need to know
Every week it seems, the public finds out about a critical piece of digital infrastructure that’s providing an unwitting vulnerability for hackers to exploit. Unless you’re a CIO or work in cybersecurity/risk mitigation, you may not even know how integral some of these systems are when the vulnerabilities are disclosed. That might be true for the most recent high-profile announcement … Read More










Dive straight into the feedback!Login below and you can start commenting using your own user instantly