Every week it seems, the public finds out about a critical piece of digital infrastructure that’s providing an unwitting vulnerability for hackers to exploit. Unless you’re a CIO or work in cybersecurity/risk mitigation, you may not even know how integral some of these systems are when the vulnerabilities are disclosed. That might be true for the most recent high-profile announcement from Apache concerning their near-ubiquitous software Log4j.
Log4j is one of those pieces of software almost no one has heard of, but upon which much of our digital infrastructure relies. At its core, it records events – errors and routine system operations – and then communicates diagnostic messages about those events to system administrators and users. Computer systems, networks systems, etc., cannot operate without these kinds of logging processes, so a vulnerability in such a critical piece of software has wide-ranging effects. For unpatched systems and machines, that vulnerability is very real — right now — and could provide threat vectors catastrophic access to your systems and data.
Here’s how to protect yourself
We talk about this a lot around here, but the first line of defense in any organization’s cyber infrastructure is keeping systems patched and up-to-date. Updating software and systems to the most recent versions, immediately upon release, is your best defense against these kinds of vulnerabilities because as companies learn about vulnerabilities, often before hackers have found them or start trying to exploit them, they patch the software to solve for that vulnerability. It’s almost always outdated software that provides the critical opening in your organization’s defenses when vulnerabilities arise.
In this particular case, the Log4Shell vulnerability opens the door for nefarious activities such as stealing sensitive information, taking control of targeted systems and slipping malicious content to other users communicating with the affected server. It can impact you, your users, your customers, your clients… all from the same vulnerability.
The vulnerability is so severe that Jen Easterly, director of the U.S. Cybersecurity & Infrastructure Security Agency, called Log4Shell the most serious vulnerability she’s seen in her career. There have already been hundreds of thousands, perhaps millions, of attempts to exploit the vulnerability.
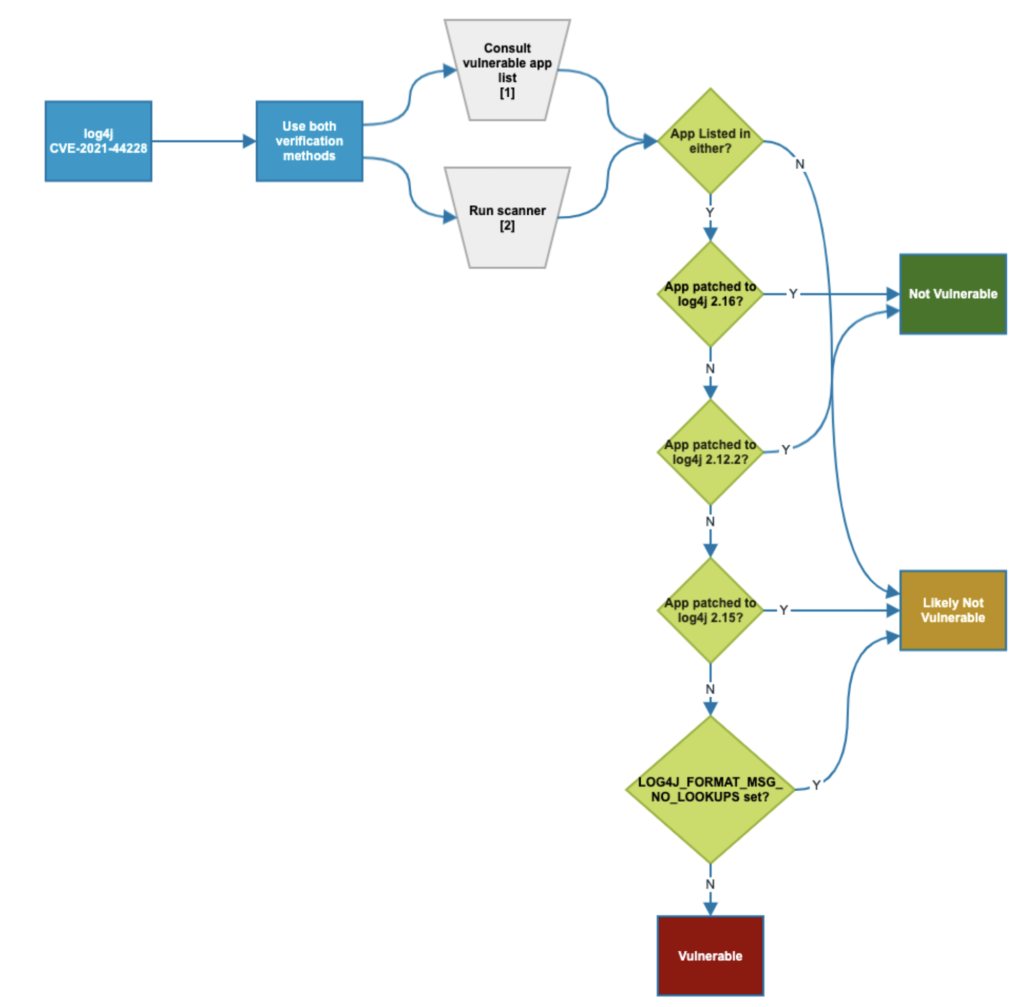
From a technical perspective, Apache’s Log4j versions 2.0-beta9 to 2.14.1 are the impacted software versions. If any of your systems are running these, the time to update was yesterday. CISA released a helpful flowchart and mitigation plan if you think or suspect your systems might be vulnerable:
- Review Apache’s Log4j Security Vulnerabilities page for additional information and, if appropriate, apply the provided workaround.
- Apply available patches immediately.
- Prioritize patching, starting with mission critical systems, internet-facing systems, and networked servers. Then prioritize patching other affected information technology and operational technology assets.
- As stated above, Emergency Directive (ED) 22-02: Mitigate Apache Log4j Vulnerability requires agencies to patch vulnerable internet-facing assets immediately.
- Conduct a security review to determine if there is a security concern or compromise. The log files for any services using affected Log4j versions will contain user-controlled strings.
- Consider reporting compromises immediately to CISA and the FBI.
How can you prevent things like this from happening in the future
At a base level, cybersecurity is an everyday kind of function. Either you or a vendor needs to be on top of this at literally all times. For Fortune 500 companies, that’s not the biggest obstacle because you have the resources and manpower to devote entire teams to this function. If, however, you’re a small or medium-sized business, you probably don’t have the time, resources or frankly the inclination to worry about this stuff constantly.
That’s where we come in. We’re experts in designing, implementing and servicing cybersecurity frameworks for clients across sectors, industries and business sizes. We keep an unblinking eye on your technology stack so you can focus on what actually matters to you — running your business. We patch vulnerabilities like Log4Shell for you, so you don’t have to worry about it impacting your company, your clients or your customers.
If you’d like to know how we can help you stay safe, give us a call — we’d love to chat.


Dive straight into the feedback!Login below and you can start commenting using your own user instantly