As we wrote about last month, cyberattacks are getting both more complex as well as destructive. For so many people, this has only meant credit card companies sending you replacement cards from time to time, or possibly Equifax offering you free credit monitoring for a year after allowing a massive data breach, or an inkling that your social security number … Read More
Is voice hacking the next line of attack for threat agents?
It’s a brave new technological world out there, and it seems to reinvent itself every couple of years. What was inconceivable only a few years ago goes from Hollywood fantasy to ubiquity in the proverbial blink of an eye. Virtual assistants like Iron Man’s J.A.R.V.I.S. leapt off the screen and into our homes via Alexa and Google Home. James Bond … Read More
President Trump signs new federal cybersecurity agency, CISA, into existence
While it might not have made nearly as much noise as the Mueller investigation, midterm upheaval or Pelosi speakership drama, there was a piece of really important legislation signed into law late last week that could have major ramifications for how much of the U.S. cybersecurity apparatus operates now and into the future. The bill, known as the CISA Act, (for “Cybersecurity and … Read More
Cryptocurrencies and blockchain are all the rage — they’ve also inspired sneaky malware you need to know about
Not all malware is designed to extort. Much of modern cyberattacks do have some sort of ransom or monetary aim, and to be sure, the ransomware do tend to get a lot of the headlines. Other malware is aimed for anarchy, like we detailed in our last post about NotPetya, the most expensive cyberattack in history. But other malware is, … Read More
$10 billion lost, a global supply chain crippled, and a miracle mistake: A NotPetya primer — cyberattack of the century
If it hadn’t been for Somali pirates, Navy Seals or the Tom Hanks movie Captain Phillips, chances are you probably wouldn’t have heard of A.P. Moller–Maersk Group, or ‘Maersk’ for short. It’s one of those companies content to work in the background, unnoticed and unknown, while at the same time fueling the entire world economy. It’s one of the largest intermodal logistics … Read More
Chinese spies used a microchip to infiltrate 30+ American tech giants… here’s what you need to know
Last week, Bloomberg Businessweek dropped the bombshell of all bombshells when it comes to cybersecurity. Everyone knows hackers are an ever-present danger in our digital lives — whether its phishing attacks, DDoS attacks, WiFi attacks, whatever — we’re always having to be on the lookout for suspicious activity throughout our digital lives. But a legit and systemic hardware attack? That’s another … Read More
Why hackers target you through IoT, how to spot a breach and how to protect yourself
In our most recent post, I walked you through the promise of the Internet of Things (IoT) from a consumer perspective before relaying a seemingly crazy anecdote about the increasingly creative (and nefarious) ways hackers are using IoT devices as access points to otherwise secure networks safeguarding sensitive data. It’s an important first step — recognizing IoT as the vulnerability … Read More
IoT does some pretty awesome stuff… and opens you up to all kinds of risk
The Internet of Things (IoT) has been on the horizon for years — in some ways, decades even. From fictional depictions as far back as the Jetsons to the promise of a smart home with intuitive tech that not only responds to your every command but can anticipate all your needs, it’s been a tantalizing frontier in consumer electronics for … Read More
Ransomware is a huge and growing problem — here’s 4 ways to protect your business
All the trend lines point one direction when it comes to ransomware frequency and scope of damage — up and to the right. A report from Cybersecurity Ventures projects that on average, there will be a ransomware attack on a business every 14 seconds by the end of 2019 — up from a rate of one attack every 40 seconds … Read More
Intel Announces Major Security Breach
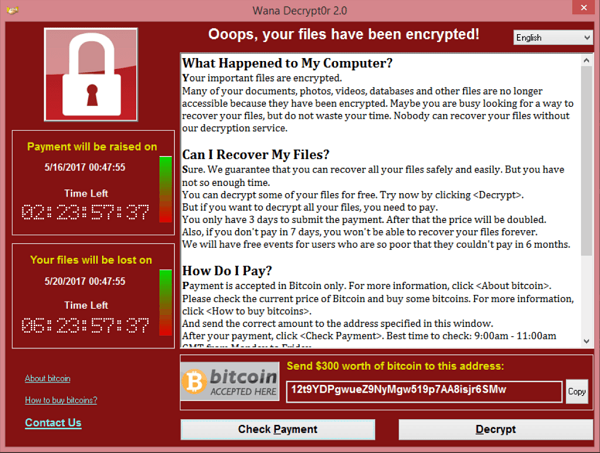
You’ve probably seen or heard about the massive security vulnerability Intel announced last week. This recent acknowledgement has the potential to dwarf the WannaCry attacks from 2017 when you consider the combined impact of attacks and performance loss. Intel Security Breach The vulnerability is at the heart of the processor architecture. This issue applies to the last 20+ years of processors … Read More








Dive straight into the feedback!Login below and you can start commenting using your own user instantly